Selamat Hari Raya Idul Fitri 1434H
Mohon Maaf Lahir dan Batin.
Semoga Ramadhan Tahun dpn udah ganti status aminnn.
Selamat Hari Raya Idul Fitri 1434H
Mohon Maaf Lahir dan Batin.
Semoga Ramadhan Tahun dpn udah ganti status aminnn.
hello and Happy Fasting All
I’d like to share about Serial Port on Rpi, kebetulan gw lagi working on Holux GPS GR-89 n mau connect to Rpi UART.note for you all, RPi UART Level itu 3.3volt and GPS gw 5v yang di take from Rpi Pins. on the out world(beuh bahasanya) maksudnya di luaran banyak yang bilang level itu must be converted, but trust me, you dont have to do that thing, just connect lah. it works!! secara umum the Raspberry Pi’s serial port is configured to be used for console input/output. Whilst this is useful if you want to login using the serial port, it means you can’t use the Serial Port in your programs, to be able to use the serial port to connect and talk to other devices (e.g. Arduino/BT-Module), the serial port console login needs to be disabled. Needless to say you will need some other way to login to the Raspberry Pi, and we suggest doing this over the network using an SSH connection, you can do this with putty(jangan jorok ye) terminal.
Just follow these instruction ya, hehe..
Disable Serial Port Login
To enable the serial port for your own use you need to disable login on the port. There are two files that need to be edited The first and main one is
/etc/inittab
This file has the command to enable the login prompt and this needs to be disabled.
Edit the file and move to the end of the file.
You will see a line similar to
T0:23:respawn:/sbin/getty -L ttyAMA0 115200 vt100
Disable it by adding a # character to the beginning.
Save the file.
#T0:23:respawn:/sbin/getty -L ttyAMA0 115200 vt100
Disable Bootup Info
When the Raspberry Pi boots up, all the bootup information is sent to the serial port. Disabling this bootup information is optional and you may want to leave this enabled as it is sometimes useful to see what is happening at bootup. If you have a device connected (i.e. Arduino) at bootup, it will receive this information over the serial port, so it is up to you to decide whether this is a problem or not.
You can disable it by editing the file
/boot/cmdline.txt
The contents of the file look like this
dwc_otg.lpm_enable=0 console=ttyAMA0,115200 kgdboc=ttyAMA0,115200 console=tty1 root=/dev/mmcblk0p2 rootfstype=ext4 elevator=deadline rootwait
Remove all references to ttyAMA0 (which is the name of the serial port). The file will now look like this
dwc_otg.lpm_enable=0 console=tty1 root=/dev/mmcblk0p2 rootfstype=ext4 elevator=deadline rootwait
Reboot
In order you enable the changes you have made, you will need to reboot the Raspberry Pi
# sudo shutdown -r now
Test the Serial Port A great way to test out the serial port is to use the minicom program.
If you dont have this installed run
# sudo apt-get install minicom
Connect your PC to the Raspberry Pi serial port using an appropriate serial port adapter and wiring, then open Putty or a similar serial terminal program on PC side. Setup a connection using the serial port at 9600 baud. Now run up minicom on the Raspberry Pi using :
# minicom -b 9600 -o -D /dev/ttyAMA0
What you type into the minicom terminal screen should appear on the serial PC terminal n sebaliknya,
this is contoh tampilan minicom lewat Putty SSH Terminal in my Win 7, I do this bcoz this is the simple way to access the Rpi.hehe..
NMEA data berhasil gw dapetin, ksananya its up to me dongs.
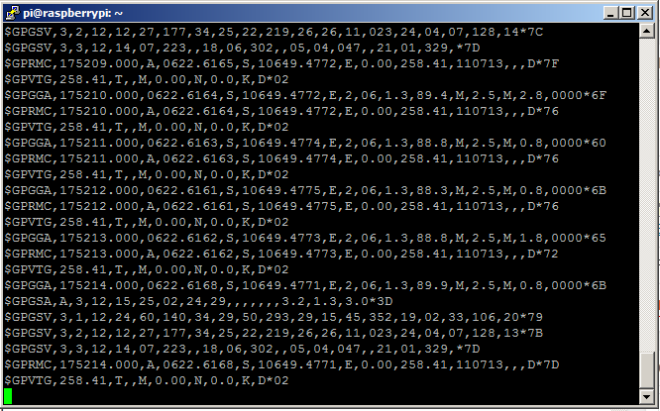
hehe.. ok, selamat mencoba kawan. ayo bobok jam stengah 4 nanti kita sahur 🙂
great things begin from the small things -tommy-
USB tethering will not work with initial default config of usb port in rasp pi, this is one of many way to connect your RPi through your android internet connection using usb tethering
Steps
1. Boot your Raspberry Pi
2. Edit the network interface configuration file
# sudo nano /etc/network/interfaces
3. Add this following line “iface usb0 inet dhcp”
auto eth0
iface eth0 inet dhcp
iface usb0 inet dhcp
4. Save the file. Ctrl-o and exit Ctrl-x
5. Run the new configuration
# sudo ifup usb0
6. Reboot your RPi
# sudo reboot
———————————–
I have try this way and succed
– RPi model B
– raspbian os
– HTC Legend with CyanogenMod
Hello..
after review the rest of my blog, I just realized that so many post that explaining about IT/UNIX hehehe…
one thing that you should know, I’m electro engineer..wkwwkwkwk
this time, I’ll post about Karman Filter, ok..lets start
Whats The Karman Filter?
first of all, you have to know about LDS( Linear Dynamical System) a partially observed stochastic process with linear dynamics and linear observations, both subject to Gaussian noise. It can be defined as follows, where X(t) is the hidden state at time t, and Y(t) is the observation.
here's the equation : x(t+1) = F*x(t) + w(t), w ~ N(0, Q), x(0) ~ N(X(0), V(0)) y(t) = H*x(t) + v(t), v ~ N(0, R)
The Kalman filter is an algorithm for performing filtering on this model, i.e., computing P(X(t) | Y(1), …, Y(t)).
The Rauch-Tung-Striebel (RTS) algorithm performs fixed-interval offline smoothing, i.e., computing P(X(t) | Y(1), …, Y(T)), for t <= T.
The Example of Karman Filter :
Here is a simple example. Consider a particle moving in the plane at constant velocity subject to random perturbations in its trajectory. The new position (x1, x2) is the old position plus the velocity (dx1, dx2) plus noise w.
[ x1(t) ] = [1 0 1 0] [ x1(t-1) ] + [ wx1 ] [ x2(t) ] [0 1 0 1] [ x2(t-1) ] [ wx2 ] [ dx1(t) ] [0 0 1 0] [ dx1(t-1) ] [ wdx1 ] [ dx2(t) ] [0 0 0 1] [ dx2(t-1) ] [ wdx2 ]
We assume we only observe the position of the particle.
[ y1(t) ] = [1 0 0 0] [ x1(t) ] + [ vx1 ]
[ y2(t) ] [0 1 0 0] [ x2(t) ] [ vx2 ]
[ dx1(t) ]
[ dx2(t) ]
Suppose we start out at position (10,10) moving to the right with velocity (1,0). We sampled a random trajectory of length 15. Below we show the filtered and smoothed trajectories.
The mean squared error of the filtered estimate is 4.9; for the smoothed estimate it is 3.2. Not only is the smoothed estimate better, but we know that it is better, as illustrated by the smaller uncertainty ellipses; this can help in e.g., data association problems. Note how the smoothed ellipses are larger at the ends, because these points have seen less data. Also, note how rapidly the filtered ellipses reach their steady-state (Ricatti) values.
here’s the code to generate the Graphs :
|——————————————————————
% X(t+1) = F X(t) + noise(Q)
% Y(t) = H X(t) + noise(R)
ss = 4; % state size
os = 2; % observation size
F = [1 0 1 0; 0 1 0 1; 0 0 1 0; 0 0 0 1];
H = [1 0 0 0; 0 1 0 0];
Q = 0.1*eye(ss);
R = 1*eye(os);
initx = [10 10 1 0]’;
initV = 10*eye(ss);
seed = 9;
rand(‘state’, seed);
randn(‘state’, seed);
T = 15;
[x,y] = sample_lds(F, H, Q, R, initx, T);
[xfilt, Vfilt, VVfilt, loglik] = kalman_filter(y, F, H, Q, R, initx, initV);
[xsmooth, Vsmooth] = kalman_smoother(y, F, H, Q, R, initx, initV);
dfilt = x([1 2],:) – xfilt([1 2],:);
mse_filt = sqrt(sum(sum(dfilt.^2)))
dsmooth = x([1 2],:) – xsmooth([1 2],:);
mse_smooth = sqrt(sum(sum(dsmooth.^2)))
subplot(2,1,1)
hold on
plot(x(1,:), x(2,:), ‘ks-‘);
plot(y(1,:), y(2,:), ‘g*’);
plot(xfilt(1,:), xfilt(2,:), ‘rx:’);
for t=1:T, plotgauss2d(xfilt(1:2,t), Vfilt(1:2, 1:2, t), 1); end
hold off
legend(‘true’, ‘observed’, ‘filtered’, 0)
xlabel(‘X1’)
ylabel(‘X2’)
subplot(2,1,2)
hold on
plot(x(1,:), x(2,:), ‘ks-‘);
plot(y(1,:), y(2,:), ‘g*’);
plot(xsmooth(1,:), xsmooth(2,:), ‘rx:’);
for t=1:T, plotgauss2d(xsmooth(1:2,t), Vsmooth(1:2, 1:2, t), 1); end
hold off
legend(‘true’, ‘observed’, ‘smoothed’, 0)
xlabel(‘X1’)
ylabel(‘X2’)
|——————————————————————
on the next post, I’ll show you how to implement this Algorithm into Simple Manipulator Robot.
Thank’s for watching..eh, thank you for reading maksudnya. wkwkwk
see you, keep on rock
long time no share. wkwkwkwk
untuk anak kosan, biasanya ini beguna lumayan, hemat patungan beli modem + internet paket++ nya si Three
yang murah.wkwkwkwkwk
oke, lets do it.
asumsikan kita udah punya modem dial-up yang udah nyambung ke internet.
dan kita mau share koneksi ini ke temen2 yang laen lewat lan/switch
the scheme-nya kira2 kayak begini cuy :
INTERNET—>PC1(ini si gateway/yang konek ke inet)—>PC2,PC3,PC4 dst… (klo lebih dari 2 pake switch bro)
oke, smua konek via networks,
di komputer yang mau di share inetnya :
(PC1 gateway/Server/yang konek ke internet)
ppp0 : konek ke inet
eth0 : konek ke temen2 yang mau nebeng/LAN
(PC2 teman2 yang mau nebeng)
eth0 : konek via lan ke PC gateway
di PC1 setting kayak gini :
IP : 192.168.0.1
Netmask : 255.255.255.0
setting via terminal-nya kek gini :
# ifconfing eth0 192.168.0.1 netmask 255.255.255.0
trs allowing the packets to forward
edit file di /etc/sysctl.conf
tambain kata2 berikut di paling bawah.
net.ipv4.ip_forward = 1
trs jalanin command berikut di terminal :
# sudo sysctl -w net.ipv4.ip_forward = “1”
trs install iptables lewat terminal
# sudo apt-get install iptables
trs jalanin command selanjutnya
# iptables -t nat-A POSTROUTING -o ppp0 -j MASQUERADE
trs install dnsmasq
# sudo apt-get install dnsmasq
trs jalanin service si dnsmasq
# sudo service dnsmasq start
nah ini bagian di komputer/PC para tebengers PC2,PC3 dst….
IP : 192.168.0.X (x ini bisa 2-254) tergantung kita mau share ke mana aja
Netmask : 255.255.255.0
Gateway : 192.168.0.1
DNS : 192.168.0.1
nah sekarang para tebengers pasti bisa konek ke internet.
klo abis restart/matiin trs iptablesnya ga jalan
ya tinggal jalanin lagi aja bro, ato bkin starup scriptnya.
nih untuk re-run iptables klo abis matiin trs gak jalan lagi sharenya
# iptables -t nat-A POSTROUTING -o ppp0 -j MASQUERADE
oke, sips…
nice to share, I’ll share the others info next time (if I have free time exactly)
thanks for reading
Regards
Tommy Agustianto
oldies but boros, ga ada bagus2nya..
VOICE DATA CALL via Modem
ATD[nomor tujuan];
jangan lupa pake titik koma, so, klo dah connect, apapun yang kita ketik di terminal kita akan muncul di terminal yang kita dial. okokok
this is the old stuff that I found in my drawer.
Wavecom Modem GPRS class II. hee…
ok, here I’ll tell you the steps to dialing up the modem
until you got an DNS from your ISP.
checking & setting modem:
1. plug in & power up your modem to serial com
2. goin to your favorite serial terminal.(minicom, gtkterm etc…)
3. example in minicom.
#minicom -s
the terminal will show you the choices and then pick portsetting
the default baudrate of wavecom is 115200
4. setting some modem parameters
in minicom that connected to your modem just enter(without double quote) :
“AT”
if correct, modem should answer
“OK”
then disable echo.
“ATE0”
setting baud
“AT+IPR=115200”
saving configurations
“AT&W”
ok, now exit minicom(ALT-Z-X)
these are the steps of dialing up:
1. make sure that you have wvdial installed, otherwise you have to install it
just enter this command at terminal :
# apt-get install wvdial
2. after you got the wvdial installed, now edit the /etc/wvdial.conf
# vim /etc/wvdial.conf
because I’m using three operator(ISP) this is the configuration
*please suit to your preferred ISP.
[Dialer Defaults]
Init1 = ATZ
Init2 = AT+CGDCONT=1,”IP”,”3gprs”
Modem Type = Analog Modem
ISDN = 0
Phone = *99***1#
Modem = /dev/ttyS0
Username = 3gprs
Password = 3gprs
Baud = 115200
save and exit from editor.
3. now for dialing up, just enter wvdial in your terminal(make sure that you’re root)
# wvdial
if success you’ll get dns and ip from your ISP.
this is the example of my success connection :
tommy@tommy-home:~$ sudo wvdial
–> WvDial: Internet dialer version 1.60
–> Initializing modem.
–> Sending: ATZ
OK
–> Sending: AT+CGDCONT=1,”IP”,”3gprs”
OK
–> Modem initialized.
–> Sending: ATDT*99***1#
–> Waiting for carrier.
CONNECT 115200
~[7f]}#@!}!}!} }6}!}$}%\}”}&} } } } }’}”}(}”}#}$@#&4~
–> Carrier detected. Waiting for prompt.
~[7f]}#@!}!}!} }6}!}$}%\}”}&} } } } }’}”}(}”}#}$@#&4~
–> PPP negotiation detected.
–> Starting pppd at Sat Jan 7 03:17:29 2012
–> Pid of pppd: 2036
–> Using interface ppp0
–> pppd: p�r ��r
–> pppd: p�r ��r
–> pppd: p�r ��r
–> pppd: p�r ��r
–> pppd: p�r ��r
–> local IP address 10.25.146.98
–> pppd: p�r ��r
–> remote IP address 192.168.111.111
–> pppd: p�r ��r
–> primary DNS address 10.0.18.54
–> pppd: p�r ��r
–> secondary DNS address 10.0.28.3
–> pppd: p�r ��r
OK, tengkyu and goodnite 🙂
1. robot explorer:
special function robot for search & rescue.
wireless control up to 100 meters
AVR Atmega16 for Controller
wireless camera with auto brightness
4 DOF Arm for Catch Something / Grip
UPDATED : DONE
2. Radar Simulation
This simulation for non-comercial
Output Image drawn to Framebuffer
2-D Vector Imaging Technology
UPDATED : DONE
3. Home Automation & Security
Automation for some kind of home appliance
PIR Sensors & Camera
Capturing Image when the Movement Sensor Triggered
UPDATED : DONE
someday if I have any spare time, I will post the picture and how them work 🙂
1. Install tftpd and related packages.
$ sudo apt-get install xinetd tftpd tftp
2. Create /etc/xinetd.d/tftp and put this entry:
service tftp
{
protocol = udp
port = 69
socket_type = dgram
wait = yes
user = nobody
server = /usr/sbin/in.tftpd
server_args = /tftpboot
disable = no
}
3. Make /tftpboot directory
$ sudo mkdir /tftpboot
$ sudo chmod -R 777 /tftpboot
$ sudo chown -R nobody /tftpboot
4. Start tftpd through xinetd
$ sudo /etc/init.d/xinetd start
Sometimes we just need a place to talk, even if no one is really listening. Although, to be honest, I really hope someone is listening!